Cloud Security
Introducing Tull, our dear friend, who’s going to explain Cloud security to us using the story of the three little pigs
What is Cloud Security
Cloud security broadly consists of technologies, controls, processes, and policies which protect your systems, data, and infrastructure hosted on the Cloud. It’s a branch of information security at large.
Cloud is a shared space, like the forest, and security is of paramount importance to the Cloud Providers. Hosted infrastructure on the Cloud, or the pig’s “house” needs to be protected from intruders seeking unauthorized access or modification, since they’re exposed and prone to attacks in the public forest. Intruders have various ways of getting access to restricted information, which broadly can be classified into “Passive” and “Active” attacks.
Active Attack
Blowing the house down, getting in through the chimney are examples of active attacks, where the wolf is directly attacking the house by finding vulnerabilities. Vulnerabilities can be in the weakness of the network structure itself (like the straw house) or a particular area which can give access to the intruder (like the chimney). The ultimate aim is to get to the house by directly attacking the structure.
Passive Attack
The act of the wolf listening and talking to the pigs and devising ways to manipulate them is an example of a passive attack. Eavesdropping, gaining private information without the knowledge of the house inmates can be classified under passive attacks. Like an active attack, the aim of the intruder is to find vulnerabilities and get into the system, but in a passive aggressive manner.
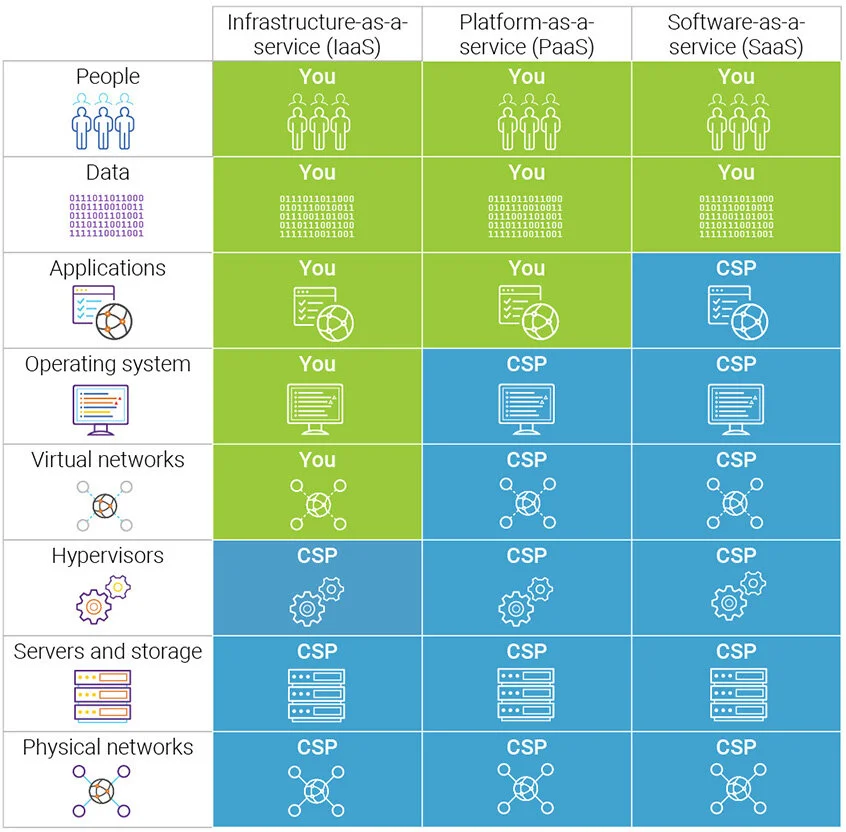
So what is a shared security Model?
Simply put, security is the shared responsibility of the vendor and the user (Cloud provider and the Organization). Here’s an infographic explaining the responsibility of the Cloud Provider (CSP) and the user depending upon the service chosen by them. (In case you missed reading my comic explaining the different cloud services, please visit the post here)
Image Source- https://www.synopsys.com/blogs/software-security/shared-responsibility-model-cloud-security/
How Do we ensure a Good security model?
Any form of information security is a complex interaction of technologies, processes, and policies established by various governing bodies. There are a widely accepted set of best practices, strategies and tools that can help you achieve a robust cloud security model.
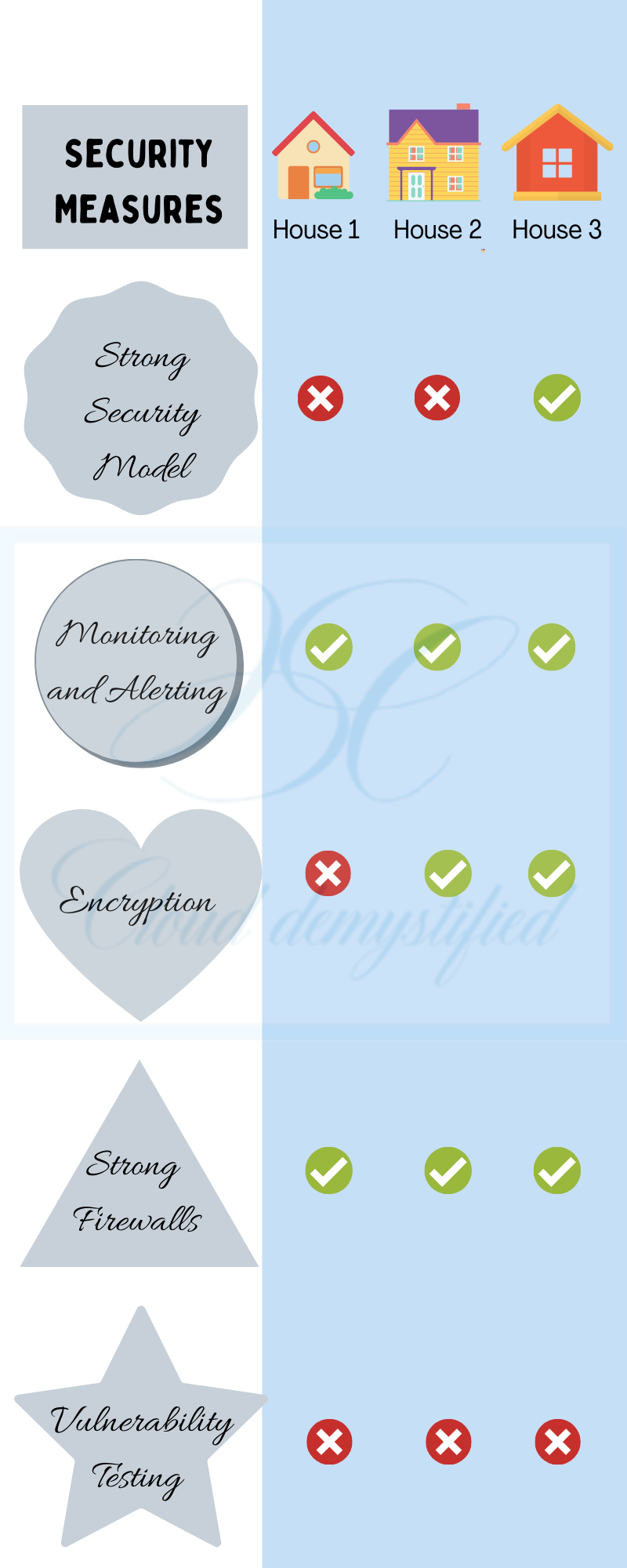
Some of the best practices are laid out below:
Identity and Access Management Control
Identity and Access Management or IAM controls, comprise of processes and policies to define the level of access each individual or a group of individuals have to the data. It’s very important to set these controls keeping in mind the model of least privilege access. This simply means giving the least amount of access to each individual or group in order to perform their work, For example, if a group of users want to just look at the data, they should be given the role of a “viewer” and not “user” or “admin”. This ensures that the data is safe, and prevents any tampering by unwanted intruders.
Another very important provision to maintain access is through a key management system provided by the Cloud Providers. A key management service is a software that allows the Organizations to create and manage the encryption keys used to protect sensitive data in their systems. Encryption keys reside in the cloud provider’s infrastructure and can only be accessed by the users who have the permissions to access them.
Active Monitoring
Actively monitoring your system helps discover potential intruders who may be lurking around and targeting your data. If the pigs had been actively monitoring the space outside their house, they would have discovered the wolf eyeing their house and practiced caution to avoid getting attacked.
Data Encryption
Encryption is the method by which all data is converted into a secret code that hides the information’s true meaning. It’s almost like the valuables hidden by the second pig inside secret vaults, due to which the wolf couldn’t access them even after breaking into the house. This ensures that the data is not accessible by anyone other than the ones allowed to access it.
Vulnerability and Penetration Testing
This complicated term means putting on the hat of the attacker and thinking like one. By this method the organizations or the Cloud service providers attack their own infrastructure to test the stability and/or discover vulnerabilities. This allows them to catch and fix vulnerabilities before any outsider can discover them.
Establishing and Managing Firewalls
Firewall is simply a wall or barrier attached to the system to avoid any intruders from getting inside. In Cloud computing, they are rules attached to systems in order to block unauthorized access while allowing outward communication. It’s like the window of the house from where the pigs could interact with the wolf, while preventing him from getting inside.
Setting security rules on incoming and outgoing traffic would help establish a barrier between the intruders and system, by filtering traffic that comes inside and blocking outsiders from gaining unwaranted access to the data.
Employee Trainings
Employees are the foundation of any organization, and adequate training on security best practices, compliance and other regulatory standards is essential to adopting a robust security model.